Python-Penetration-Testing-Essentials-Second-Edition/port.txt at master · PacktPublishing/Python-Penetration-Testing-Essentials-Second-Edition · GitHub

Hacking Articles on Twitter: "Common Ports Cheat Sheet https://t.co/62PMMHvy3o #infosec #cybersecurity #cybersecuritytips # pentesting #oscp #redteam #informationsecurity #cissp #CyberSec #networking #networksecurity #CheatSheet #infosecurity ...

Interview #common #questions TCP/UDP port numbers. For cyber security professionals you can also think about the payloads you can use if these ports are open. #indincybersecuritysolutions #cybersecurity... - Indian Cyber Security Solutions -


![How to attack an infrastructure using VoIP exploitation [Tutorial] | Packt Hub How to attack an infrastructure using VoIP exploitation [Tutorial] | Packt Hub](https://packt-type-cloud.s3.amazonaws.com/uploads/sites/2432/2018/06/5e8d8982-3c95-48ca-bae9-9656fa4bfaa2.png)

![How to attack an infrastructure using VoIP exploitation [Tutorial] | Packt Hub How to attack an infrastructure using VoIP exploitation [Tutorial] | Packt Hub](https://packt-type-cloud.s3.amazonaws.com/uploads/sites/2432/2018/06/8e94a4b8-5b79-40a9-be92-abe3ad36cc29.png)




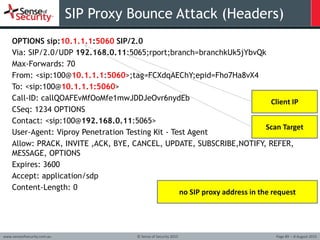
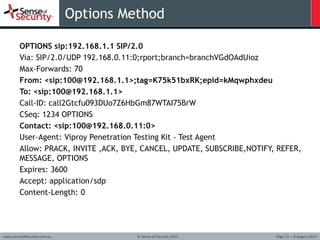


![How to attack an infrastructure using VoIP exploitation [Tutorial] | Packt Hub How to attack an infrastructure using VoIP exploitation [Tutorial] | Packt Hub](https://packt-type-cloud.s3.amazonaws.com/uploads/sites/2432/2018/06/b534d740-13bf-4799-8835-d7940f267db5.png)


